Hacking is a professional industry
The road to cyberattacks is all about finding the security breaches within a company. It compares to when a thief goes from door to door along a residential street to examine if there is an open door in one of the houses, and when the thief enters, he makes sure all the possible backdoors are free to be able to find a quick exit again. Both large and small companies are at risk.
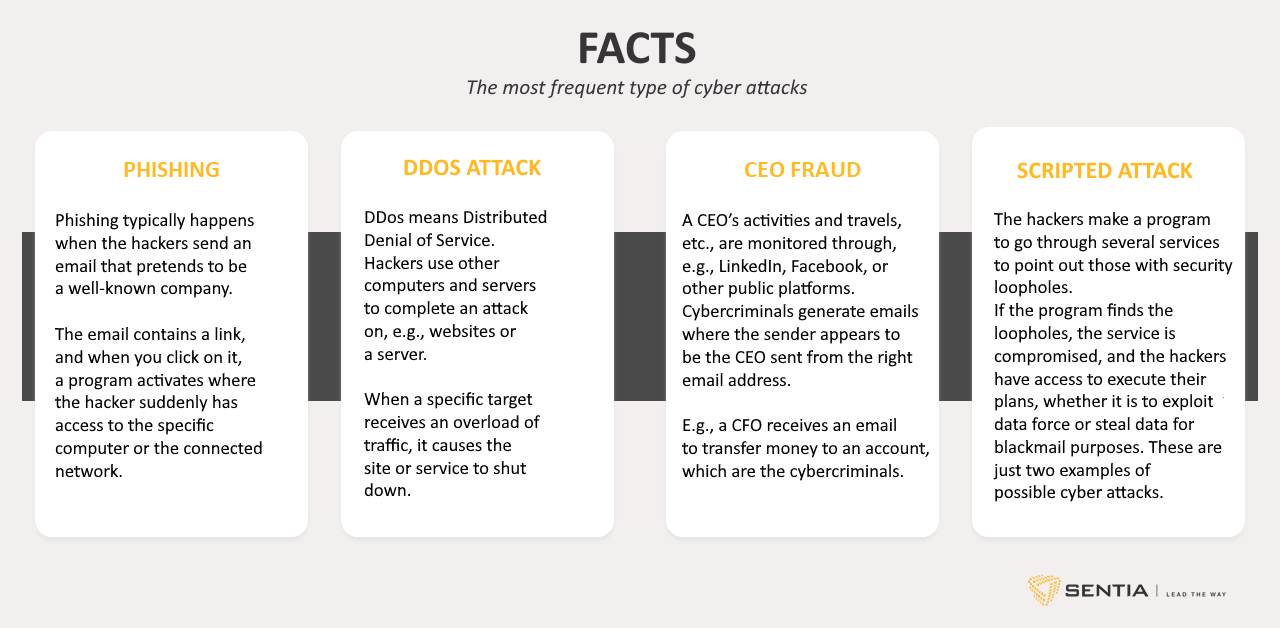
Cybercriminals continuously check for the many vulnerabilities that occur when, for example, new versions of CMS systems are announced. It is often the case that companies do not update the website to the latest version, and this opens up for cybercriminals to do damage. Websites are more vulnerable because they are exposed to the internet 24/7, whereas a company’s internal systems are often better protected.
It is not difficult to figure out which systems appear in new versions, as one can search for it in the public databases. The hackers have set up programs that frequently check if companies have updated to the latest versions, or if there is a security breach - and when there is, they strike. And like thieves in the physical world, hackers make sure to have a backdoor open so they can get away again without leaving a trace.
Who are the hackers and what do they want?
The criminals are thus looking for data power, which is used for criminal purposes, and of course, money. It can, for example, result in various forms of extortion of companies, which with ransomware, get their data locked and then are threatened to pay in order to unlock the data again. Another reason for hacking companies' systems is to use the methods for cryptocurrency mining. Still, it can also be a far greater economic crime in the form of money laundering that is the background for an attack.
Cybercrime is no longer just something that goes on from a lurky basement. It is a professional business with people who go to work and attack companies between 9 am and 5 pm. We can see this at the times when we register attempted attacks. It takes place during working hours from Monday to Friday, for example, from e.g. China or Russia, and everyone can order an attack. There are even customer service and transparent agreements on delivery etc. at the criminal companies. So, there is good reason to secure your business professionally.